
Your household appliances can be hacked
The neighbour’s kid hacks your washing machine and terrorists switch off the power in your city. These are likely future scenarios with modern technology. But now a researcher has set out to combat this.
Printers that print hundreds of weird-looking images, washing machines that start running at night, or air conditioning that turns department stores or hospitals into freezers.
In modern buildings, an increasing number of electrical devices are connected to wireless networks, and that increases the risk of criminals hacking into the building and causing havoc.
“It could for instance be your neighbour’s naughty son who hacks into your system and takes control of the heating and lighting in your house,” says Ender Yüksel, a postdoc at the Department of Informatics and Mathematical Modelling at the Technical University of Denmark (DTU).
”But obviously, it would be a lot worse if terrorists were to hack into a hospital or turn off the power supply in large areas.”
Homes can be hacked
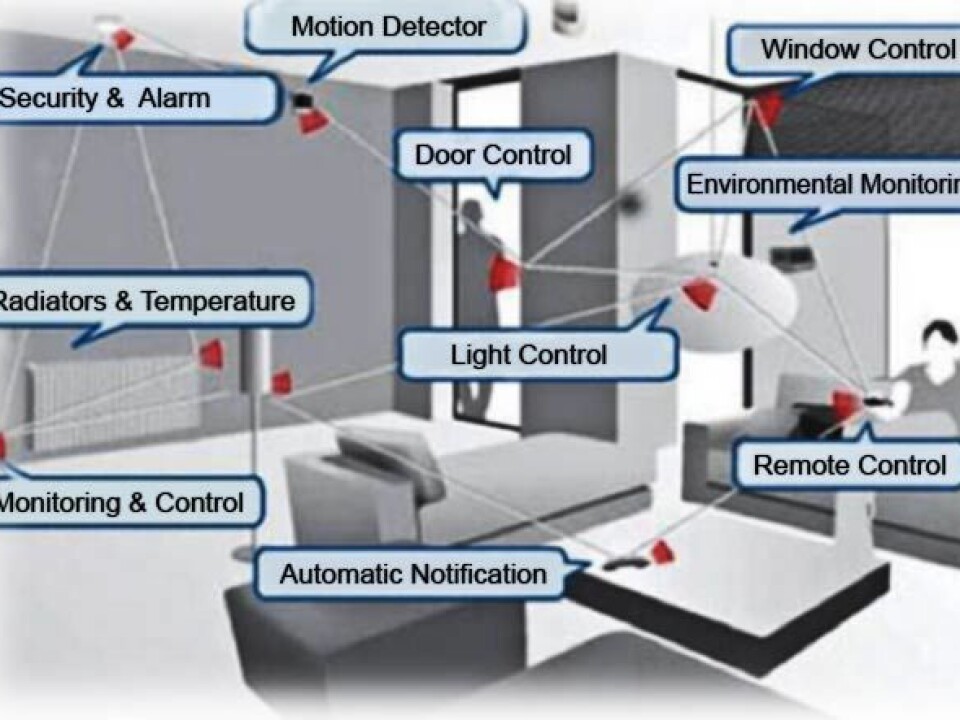
Yüksel has spent the past five years studying how people can guard themselves against hacker attacks on so-called wireless sensor networks.
These networks consist of electrical sensors, which can measure and control temperature, light, power and other features in a building.
The sensors transmit the data via a wireless sensor network to one another and to a control station, which could for instance be a computer or a mobile phone.
This type of network is already being used in industrial buildings across the world, and in the near future it will also be part of modern homes.
Architects and engineers of communication standards and manufacturers of network devices have made several efforts to improve security. But we scientists have nevertheless repeatedly shown that the security procedures are insufficient.
“When you’re abroad, you’ll be able to control the temperature in your house with your smartphone, or you could start your washer while you’re at work,” he says.
“This will make our lives easier, but it also entails a risk that our homes can be hacked.”
Insufficient security
Together with colleagues, Yüksel has studied the security procedures in a variety of sensor networks, and he believes these studies prove that it’s relatively easy to gain free access to other people’s electrical appliances.
“Architects and engineers of communication standards and manufacturers of network devices have made several efforts to improve security. But we scientists have nevertheless repeatedly shown that the security procedures are insufficient.”
The use of probability theory in relation to security is completely new.
If, say, a thief steals a little sensor from a hospital, it would be relatively easy to break the sensor’s code and gain access to the rest of the sensor network. This enables the thief to control all sensors at the hospital – for instance to shut off the power supply to essential appliances.
“It requires some expertise, but for a professional, this wouldn’t take more than five minutes,” says Yüksel.
“That’s the equivalent of a thief stealing the caretaker’s master key and suddenly opening all doors in a building.”
Maths as a weapon against hackers
But how do you protect a building from hackers then?
Up until now, IT security has been regarded in a ‘black or white’ way, meaning that a system was either secure or not secure. But instead of saying that a system is insecure, we can now say that there’s a risk of, say, five percent that a system will be hacked.
In his research, Yüksel used a surprising weapon against the hackers – mathematics.
Using a complex form of probability theory, he came up with some mathematical models that can calculate the risk of a particular sensor network getting hacked.
“The use of probability theory in relation to security is completely new,” he says.
“Up until now, IT security has been regarded in a ‘black or white’ way, meaning that a system was either secure or not secure. But instead of saying that a system is insecure, we can now say that there’s a risk of, say, five percent that a system will be hacked.”
The code must be changed
He explains that there can be a variety of strategies for how to safeguard a sensor network against uninvited hacker guests.
The network contains a security key, which is comparable to a password to an email or online banking account. The longer you use the same password, the greater the risk that the code is broken, so that strangers gain access to personal emails or bank accounts.
“That’s why you should have a strategy for when to change the password to your email account,” he says.
“It could be every six months or perhaps every time you’ve used a public computer. Similarly, you should have a strategy for when and how the security key to a sensor network is changed.”
Energy vs. security
The downside to updating the security key on a sensor network is that it requires extra energy, says the researcher.
This could be problematic because the small sensor nodes that link the various appliances to the network usually run on batteries.
So you may not wish to update the security key too often because then you would constantly need to change the batteries. You need to find a balance between security on the one hand and energy on the other, he explains.
“The software I have developed enables the user to specify e.g. that the batteries should last at least two years. From there, the model will calculate which strategy you need for your wireless sensor network to be as secure as possible.”
-----------------------------------------
Read the Danish version of this article at videnskab.dk
Translated by: Dann Vinther





